Virtual Private Network Servers
DBM Virtual Private Network server establish secure connections between your on-premises networks, remote offices, client devices, and the DBM global network. DBM VPN is comprised of three services: Site-to-Site VPN, Remote access VPN and Personal VPN. Each service provides a highly-available, managed, and elastic VPN solution to protect your network traffic.
DBM Supported 2 Types of VPN
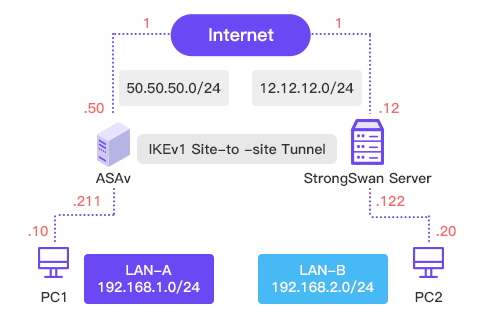
Solution 1 – Site-to-Site VPN
Prerequisites: Dedicated Server + ASA Firewall, Shared ASA or Dedicated ASA are available.
The Cisco Hardware firewall supports site-to-site VPN for a single gateway-to-gateway VPN tunnel. For example, you can configure the Cisco Hardware firewall at a branch site to connect to the router at the corporate site, so that the branch site can securely access the corporate network.
When configuring Site-to-Site VPN, a form must be filled out by the customer and configured both on the DBM side and locally by the customer.
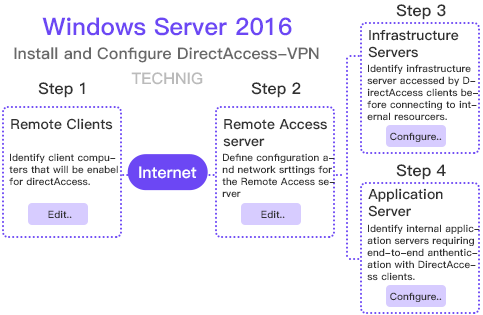
Solution 2 – Personal VPN
Prerequisite: Windows VPS, Dedicated Windows Server
In Windows Server 2016 and Windows Server 2012, you can deploy both DirectAccess and Routing and Remote Access Service (RRAS) on the same server. These allowing you to provide DirectAccess connectivity to supported clients as well as providing VPN access to remote clients that do not support.
About Cisco Hardware Firewall
A reliable firewall is the hallmark of a secure network. Networks support sensitive, crucial applications and processes, and provide a common infrastructure for converged data, voice, and video services. Firewall security is a primary concern. Instead of providing only point products that set a base level of security, Cisco embeds firewall security throughout the network and integrates security services in all of its products. Firewall security becomes a transparent, scalable, and manageable aspect of the business infrastructure.
Cisco ASA 5500 Series Adaptive Security Appliances are easy-to-deploy solutions that integrate world-class firewall, Unified Communications (voice/video) security, SSL and IPsec VPN, intrusion prevention (IPS), and content security services in a flexible, modular product family.
| Item | Description | One-Time Fee | Monthly Fee | Notes |
|---|---|---|---|---|
| Cisco Hardware Firewall | Includes 10-user license, 8-port Fast Ethernet switch, stateful firewall, 10 IPsec VPN peers, 2 SSL VPN peers, 3DES/AES license, and 1 expansion slot | $0.00 | $49.00 | -- |
| Dedicated Server | 1u Supermicro Super Server Quad-Core Xeon E5-1620v2 CPU 64GB RAM 2x960GB SSD RAID 1 + 2TB SATA Windows Server 2019 Standard Edition x64 | $0.00 | $199.00 | -- |
| Total | $0.00 | $248.00 | -- |
Types of VPN Server Supported
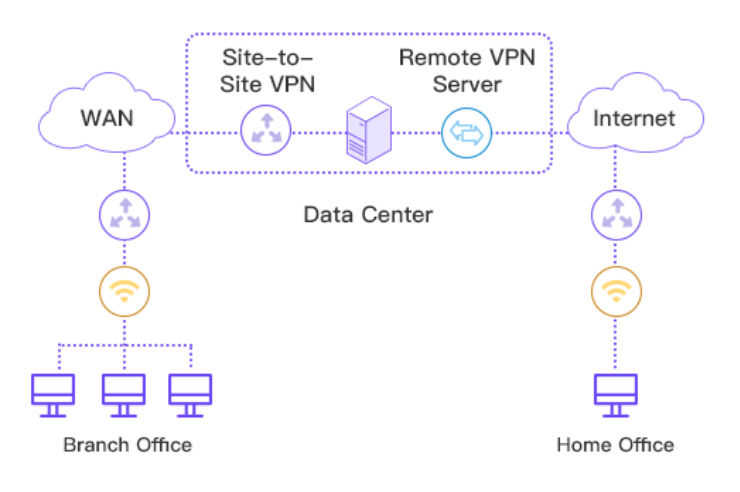
Site-to-site VPN(aka Network-based VPN)
Remote access VPN(aka Client VPN、Business VPN)
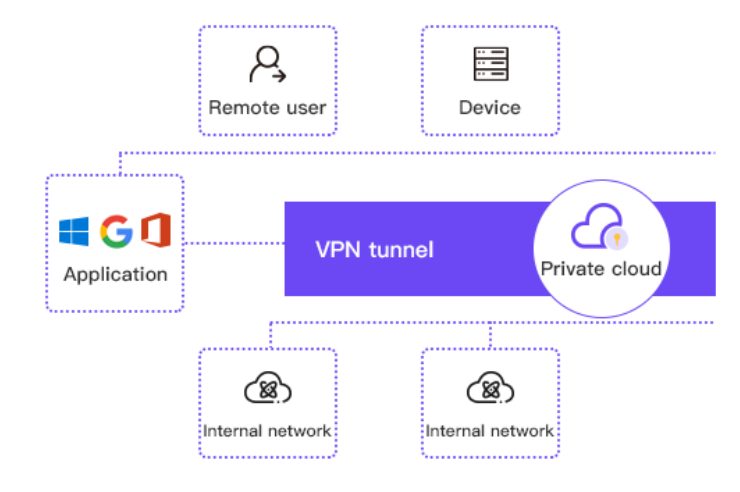
Personal VPN(aka Consumer VPN)
Comparison of VPN types
| Site-to-Site VPN | Remote Access VPN | Personal VPN | ||
|---|---|---|---|---|
| Who Connects Where? | Network connects to another network. | User connects to a private network. | User connects to the internet via a third-party server | |
| Software Required? | Users do not need to run additional software. | Users usually need install software on their device,or configure their operating system. | Users install a VPN service’s software onto their device. | |
| Best Used For | Joining up two or more networks,to create a combined single network. | Connecting to your company’s network or any other private network form home or another remote location. | Protecting your privacy and bypassing geographic restrictions online. |

Cisco ASA 5500 Series Adaptive Security Appliances Documents

The 4 Main Types of VPN

How to connect to remote access VPN from Win10

Set up a VPN connection on Mac

Configuring a Site-to-Site VPN Tunnel Between RV Series Routers and ASA 5500 Series Adaptive Security Appliances
VPN Server FAQs
What does L2TP mean in VPN?
Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data. L2TP protocol is based on the client/server model.
What is IPSec VPN?
IPsec VPN is a protocol, consists of set of standards used to establish a VPN connection. A VPN provides a means by which remote computers communicate securely across a public WAN such as the Internet. A VPN connection can link two LANs (site-to-site VPN) or a remote dial-up user and a LAN.
What is IPSec VPN and how it works?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
What is the difference between ISAKMP and IPsec?
ISAKMP, also called IKE (Internet Key Exchange), is the negotiation protocol that allows hosts to agree on how to build an IPSec security association. ISAKMP is part of the internet key exchange for setting up phase one on the tunnel. IKE establishes the shared security policy and authenticated keys. ISAKMP is the protocol that specifies the mechanics of the key exchange.
IPsec combines three main protocols to form a security framework:
1. Internet Key Exchange (IKE) protocol
2. Encapsulating Security Payload (ESP) protocol
3. Authentication Header (AH) protocol
What does IKEv2 mean in VPN?
Internet Key Exchange version 2 (IKEv2) is an IPsec based tunneling protocol that provides a secure VPN communication channel between peer VPN devices and defines negotiation and authentication for IPsec security associations (SAs) in a protected manner.

























































